Configuring Proxy ARP for Manual NAT
Symptoms
- After creating a Manual Static NAT rule, Security Gateway does not answer the ARP Requests for the Static NATed IP address that was configured in the Manual NAT rule.
- Security Gateway replies to ARP requests with a wrong MAC address, mostly for the NAT traffic.
Introduction
Let us consider the following scenario:
- Two networks (Network_A and Network_B) are separated by a Security Gateway (single Security Gateway or ClusterXL).
- On each network, there is a host (Host_A on Network_A, Host_B on Network_B).
- Let us assume, that Network_A represents the Internal network, and Network_B represents the External network.
- According to the existing standards, when Host_B needs to send data to Host_A, an ARP Request for the MAC address of Host_A will be sent by Host_B to Network_B.
Since Host_A is located on another network, and the Security Gateway acts as a router, this ARP Request (sent to Broadcast address on Layer2) will not be forwarded by the Security Gateway from Network_B to Network_A.
As a result, Host_B will not discover the MAC address of Host_A, and will not be able to send the data to Host_A.
A standard solution, in such cases, is to configure the Security Gateway to act as Proxy ARP.
The Security Gateway will pretend to be the Host in question. The Security Gateway will accept the ARP Requests and the Security Gateway will send its own MAC Address in ARP Reply. Then, when the data is received from the External network, the Security Gateway will forward the data to the relevant host on the Internal network.
STEP 1: Configuration principles
Configuration for Proxy ARP is two-fold:- Configuring Layer2-to-Layer3 matching on Security Gateway / each cluster member - matching IP addresses of the relevant hosts on the Internal network (where the hosts are located) to the MAC Address of the Security Gateway on the External network (where the IP addresses of these hosts should be published).
On Check Point Security Gateway / Cluster member, this matching is saved in the $FWDIR/conf/local.arp file. - Creating relevant Manual NAT rules in SmartDashboard and installing the policy.
STEP 2: Procedures
- Procedure for Gaia OS in Gateway mode - R76 / R77 / R77.10 and above
Important Notes:
- Changes to Proxy ARP list made in Gaia Clish / Gaia Portal will take effect only after policy installation.
- Since Gaia R77.10, it is possible to configure Proxy ARP entries in Gaia Portal:
Go to Network Management section - click on ARP page - scroll down to the Proxy ARP section - click on Add button.
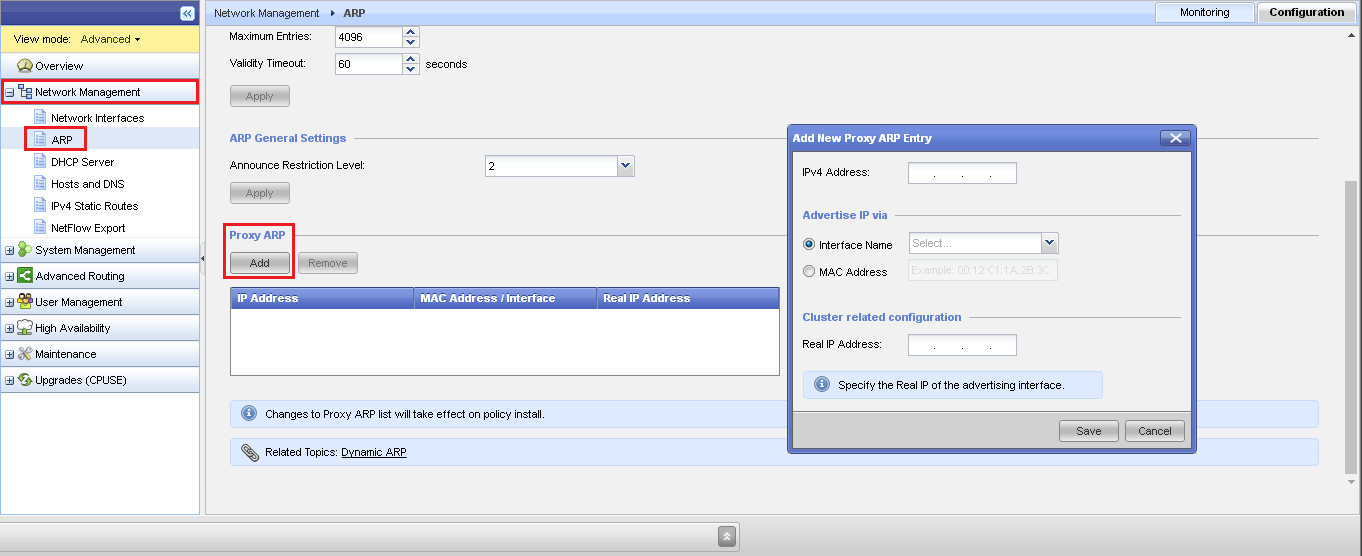
Note: In cluster environment, in the "Real IP Address" field, enter the real IP address of member's physical interface on external network. - Since Gaia R76, user has to configure Proxy ARP entries in Gaia Clish using the add arp proxy ipv4-address ... command (the $FWDIR/conf/local.arp file will be created by Gaia OS):
Clarification:Method Syntax in Gaia Clish via
'interface'
(recommended)HostName:0> add arp proxy ipv4-address IP_ADDRESS_OF_HOST_THAT_SHOULD_BE_PUBLISHED interface NAME_OF_ADVERTISING_INTERFACE_ON_EXTERNAL_NETWORK real-ipv4-address REAL_IP_ADDRESS_OF_ADVERTISING_INTERFACE_ON_EXTERNAL_NETWORK
HostName:0> save configvia
'macaddress'HostName:0> add arp proxy ipv4-address IP_ADDRESS_OF_HOST_THAT_SHOULD_BE_PUBLISHED macaddress MAC_ADDRESS_OF_ADVERTISING_INTERFACE_ON_EXTERNAL_NETWORK real-ipv4-address REAL_IP_ADDRESS_OF_ADVERTISING_INTERFACE_ON_EXTERNAL_NETWORK
HostName:0> save config
- Both configuration methods are accepted.
- The first method add arp proxy ipv4-address ... interface ... is easier and is recommended:
- Using the names of the interfaces is more intuitive
- Clish will display the available interfaces when pressing Tab key after interface
- MAC address of the selected interface will be used automatically
- To configure multiple Proxy ARP entries at once, user can create a plain-text file with the relevant add arp proxy ipv4-address ... commands,
and then run the following command:
[Expert@HostName:0]# clish -s -f /path_to/file_with_proxy_arp_syntax.txt - Any change in Proxy ARP made in Gaia Clish / Gaia Portal, will override any manual changes in the $FWDIR/conf/local.arp file.
- Proxy ARP configuration made in Gaia Clish / Gaia Portal (and saved in Gaia Database), during boot will override any manual changes in the $FWDIR/conf/local.arp file.
- To remove a Proxy ARP entry:
Where How In Gaia Clish HostName:0> delete arp proxy ipv4-address IP_ADDRESS_OF_HOST_THAT_SHOULD_BE_PUBLISHED
HostName:0> save configIn Gaia Portal - Go to Network Management section - click on ARP page
- In the Proxy ARP section, select the relevant entry - click on Remove button
- To display the configured ARP Proxy entries:
Where to run Which commands to run In Gaia Clish - either
HostName:0> show arp proxy all - or
HostName:0> show arp proxy ipv4-address IP_ADDRESS_OF_HOST_THAT_SHOULD_BE_PUBLISHED
In Expert mode - [Expert@HostName:0]# grep arpproxy /config/db/initial
- either
Procedure:
- Connect to the command line on Security Gateway / each cluster member (over SSH, or console).
- Log in to the Clish.
- Add the relevant Proxy ARP entries:
Each entry contains:
- IP address of the relevant host that should be published to the outside world
- Name of the relevant Security Gateway's advertising interface on the External network;
or MAC address of the relevant Security Gateway's advertising interface on the External network - Real IP address of advertising interface
- Connect with SmartDashboard to Security Management Server / Domain Management Server.
- In SmartDashboard, create a Host object that will represent the relevant host on the Internal network (Internal IP address).
- In SmartDashboard, go to Policy menu - click on Global Properties - go to NAT pane - go to Automatic NAT rules section.
If the box "Automatic ARP configuration" is checked, then also check the box "Merge manual proxy ARP configuration".
or
Disable the "Automatic ARP configuration" completely (clear the box).
Notes:
- Automatic ARP Configuration is enabled by default - it ensures that ARP requests for a translated (NATed) machine, network or address range are answered by the Security Gateway.
- Merge manual proxy ARP configuration merges the Automatic and Manual ARP configurations. Manual proxy ARP configuration is required for manual Static NAT rules. If a manual ARP configuration is defined in the $FWDIR/conf/local.arp file, and "Automatic ARP configuration" is enabled, both definitions are maintained. If there is a conflict between the definitions (the same NATed IP address appears in both), then the manual configuration is used.
- If "Automatic ARP configuration" setting is enabled, but "Merge manual proxy ARP configuration" setting is not enabled, then the Security Gateway ignores the Proxy ARP entries in the $FWDIR/conf/local.arp file.
- In SmartDashboard, go to Policy menu - click on Global Properties - go to Manual NAT rules section.
Check the box "Translate destination on client side".
Notes:
- Translate destination on client side is enabled by default - it applies to packets originating at a Client, with the Server as its destination. Static NAT for the server is performed on the Client side of the Security Gateway.
- Create the following Manual NAT rules:
- In R80 SmartConsole:
No. Original
SourceOriginal
DestinationOriginal
ServicesTranslated
SourceTranslated
DestinationTranslated
Services1 object that represents
the relevant host
on the Internal network
(with its Internal IP address)* Any* Any'Static' translation -
object that represents
the External (NATed)
IP address of
the relevant host= Original= Original2 * Anyobject that represents
the External (NATed)
IP address of
the relevant host* Any= Originalobject that represents
the relevant host
on the Internal network
(with its Internal IP address)= Original - In R7x SmartDashboard:
No. Original Packet Translated Packet Source Destination Service Source Destination Service 1 object that represents
the relevant host
on the Internal network
(with its Internal IP address)AnyAny'Static' translation -
object that represents
the External (NATed)
IP address of
the relevant host= Original= Original2 Anyobject that represents
the External (NATed)
IP address of
the relevant hostAny= Originalobject that represents
the relevant host
on the Internal network
(with its Internal IP address)= Original
- In R80 SmartConsole:
- Install the Security Policy.
- Check the Proxy ARP table on Security Gateway / each cluster member using the following commands in Expert mode:
- [Expert@HostName:0]# fw ctl arp
Sample output:
[Expert@Member_A]# fw ctl arp (192.168.176.143) at 00-1c-7f-00-00-f8 interface 172.16.176.5 and [Expert@Member_B]# fw ctl arp (192.168.176.196) at 00-1c-7f-00-00-f8 interface 172.16.176.6 where the physical is .5 and .6 for the cluster members - [Expert@HostName:0]# fw ctl arp -n
- [Expert@HostName:0]# arp -a
- [Expert@HostName:0]# arp -e
- [Expert@HostName:0]# fw ctl arp
Comments
Post a Comment