Malware Displaying Porn Ads Discovered in Game Apps on Google Play
Check Point Researchers have revealed a new and nasty malicious code on Google Play Store that hides itself inside roughly 60 game apps, several of which are intended for children. According to Google Play’s data, the apps have been downloaded between 3 million and 7 million times.
Dubbed ‘AdultSwine’, these malicious apps wreak havoc in three possible ways:
- Displaying ads from the web that are often highly inappropriate and pornographic.
- Attempting to trick users into installing fake ‘security apps’.
- Inducing users to register to premium services at the user’s expense.
In addition, the malicious code can be used to open the door for other attacks such as user credential theft.
How It Works
Once the malicious app is installed on the device, it waits for a boot to occur or for a user to unlock their screen in order to initiate the attack. The attacker then selects which of the above three actions to take and then displays it on the device owner’s screen.
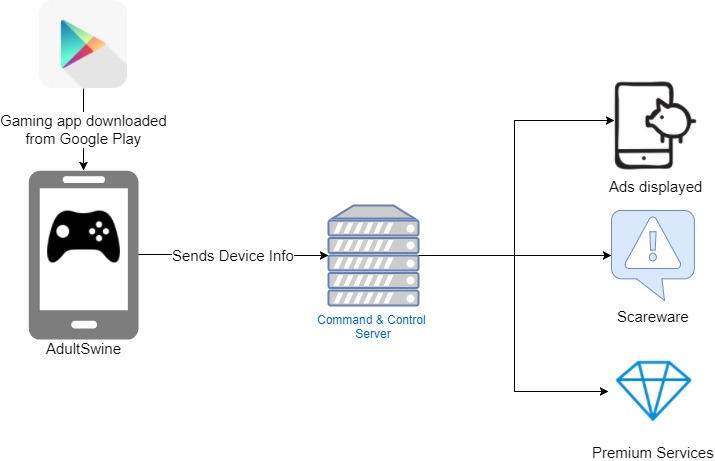
Figure 1: ‘AdultSwine’ Operation Flow
Inappropriate and Pornographic Ads
The most shocking element of this malicious app is its ability to cause pornographic ads (from the attacker’s 3rd party library) to pop up without warning on the screen over the legitimate game app being displayed.
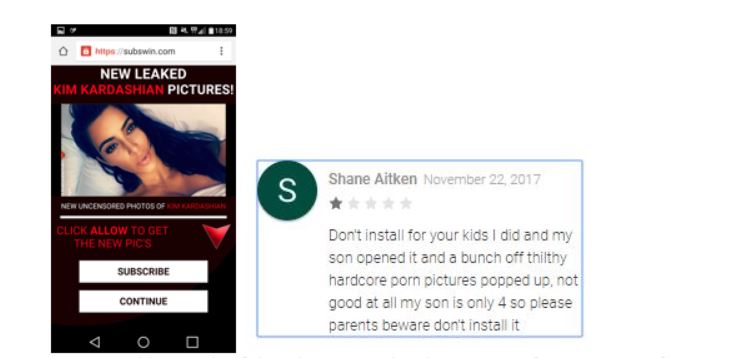
Figure 2: A mild example of the ads presented and a comment from a parent of a four-year old victim.
Scareware – Deceptive App Install Tactics
Another course of action the malicious app pursues is scaring users into installing unnecessary and possibly harmful “security” apps.
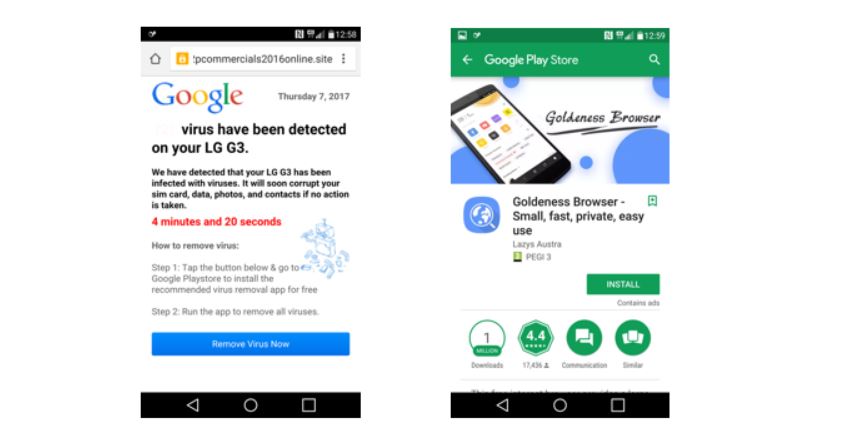
First, the malicious app displays a misleading ad claiming a virus has infected the user’s device.
Upon selecting the ‘Remove Virus Now’ call to action, the user is directed to another app in the Google Play Store posing as a virus removal solution.
The “virus removal solution” is anything but – it’s another fake app.
Registering To Premium Services
Another technique used by the malicious app is registering to premium services and charging the victim’s account for fraudulent premium services they did not request. In a similar way to the scareware tactic presented above, the malicious app initially displays a pop-up ad, which attempts to persuade the user to register for this service.
This time however, the ad claims that the user is entitled to win an iPhone by simply answering four short questions. Should the user answer them, the page informs the user that he has been successful, and asks him to enter his phone number to receive the prize. Once entered, the ad itself then uses this number to register to premium services.
Decisive Corrective Action
Upon being advised of our findings, Google collaborated with Check Point Research, took prompt action to remove affected apps from Play, disabled the developers’ accounts, and will continue to show strong warnings to any users that still have the apps installed.
The scareware “virus removal solution” was suspended from Google Play for using inappropriate marketing tactics to drive installs.
Takeaways
Apps infected with the nasty ‘AdultSwine’ malicious code are able to cause emotional and financial distress.
Due to the pervasive use of mobile apps, ‘AdultSwine’ and other similar malicious apps will likely be continually repeated and imitated by hackers. Users should be extra vigilant when installing apps, particularly those intended for use by children. We advise parents to verify that apps used by their children are categorized as “Designed for Families” on Google Play.
Effective protection from attack by these malicious apps, requires users to install advanced mobile threat defense solutions such as Check Point SandBlast Mobile and Check Point Zone Alarm on all mobile devices.
For more full details of the research, please visit our Research Blog.
Check out the interview with our CMO, Peter Alexander, as he recently caught up with ABC Bay Area to talk about AdultSwine.

Comments
Post a Comment